 Trying to remember a time before the World Wide Web, personal computers, iPads, and smart phones is comparable to trying to imagine a time before there were cars and highways. How did we ever get anything done? The advantages of the information age allow humankind to access and share massive amounts of information, perform commerce, and interact across diverse populaces on a grander and more rapid way than ever imagined when that first Apple PC appeared the late 1970s. However, as with all great and amazing human achievements and technology advances, new dangers and threats emerge that we must defend against.
Trying to remember a time before the World Wide Web, personal computers, iPads, and smart phones is comparable to trying to imagine a time before there were cars and highways. How did we ever get anything done? The advantages of the information age allow humankind to access and share massive amounts of information, perform commerce, and interact across diverse populaces on a grander and more rapid way than ever imagined when that first Apple PC appeared the late 1970s. However, as with all great and amazing human achievements and technology advances, new dangers and threats emerge that we must defend against.
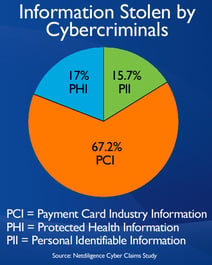 One such threat are cyber criminals. They lurk in the dark corners of the World Wide Web waiting to steal your personal and private information, obtain your username and passwords, access your bank account or credit cards, and to sabotage your personal computer. According to a Netdiligence Cyber Claims Study, the most common information stolen by cybercriminals is payment card information, such as credit and debit card numbers. And human error is still one of the biggest reasons cyber criminals gain access to your information. Here are a couple things we all can do to defend against these cyber scoundrels.
One such threat are cyber criminals. They lurk in the dark corners of the World Wide Web waiting to steal your personal and private information, obtain your username and passwords, access your bank account or credit cards, and to sabotage your personal computer. According to a Netdiligence Cyber Claims Study, the most common information stolen by cybercriminals is payment card information, such as credit and debit card numbers. And human error is still one of the biggest reasons cyber criminals gain access to your information. Here are a couple things we all can do to defend against these cyber scoundrels.
Phishing anyone?
Phishing has become one of the most common methods that cyber criminals use to get your sensitive information. In fact, over 90% of data breaches start with a phishing attack. Phishing is when a cyber criminal sends a fraudulent email message that impersonates a legitimate person, company, or organization. Because these emails look so real, they trick recipients into clicking on links, downloading harmful attachments, or entering personal information.
Here is an example of a phishing emails. You get an email from a friend, someone you have known for years. The email might say, “Hey there, so nice seeing you last year. Pictures from the event are located in this Google Dropbox (or an attachment). Feel free to share with your friends and family. But, when you click on the link or the attachment to see the pictures, a virus is downloaded.
So how can you protect yourself? If it doesn’t feel right, don’t click. Check with the source via a phone call, or sending a separate email. Also, check out that email address of person who sent the email. Phishing emails almost always use fake email addresses. Cyber criminals like to use misspelled email addresses that look very similar to well-known companies, brands, or people to trick their victims into reading it. Another thing you can do is hover the mouse over and links that are in the email, BUT don’t click on it. The actual URL (Internet address) will appear. If the email is supposedly from Amazon, but the URL shown says something else, delete the email.
If you would like to learn more tips on how to spot an email, visit: https://blog.imon.net/how-to-spot-a-phishing-email
How do they know so much about me?
Social media connects people with each other from different walks of life and interests. The cyber criminals aren’t lazy. They do their homework. They follow social media like Facebook, Twitter, Instagram, LinkedIn etc. Then, they connect the dots from the information people post about themselves and use it to gain people’s trust. So, make sure you and your family are not sharing too much information on your social media accounts.
Security Awareness
If you have a computer or a mobile device connected to the Internet, it will be hacked. But one way to protect yourself is to up-to-date protection on your devices. One option is to invest in ImOn’s TechHome. TechHome offers industry-leading desktop security protection and Internet security to protect you against the latest online threats.
You should also use passwords to help protect our personal information and devices. While there is no such thing as a perfect password, you can make it strong enough, so hackers will likely get discouraged and give up before it is cracked. Strong passwords should have at least 8-12 characters and contain a combination of upper and lower case letters, numbers, and symbols. To learn more about what makes a strong password, visit: https://blog.imon.net/2016/08/31/creating-strong-passwords.
But remember, a password is no good if you don’t use it. You should make sure to enable an automatic locking screen on your tablet and smartphone. It is also recommended that you logoff, or lock, your computer and laptop every time you are finished, or when you are leaving the room. This ensures that if your device is lost or stolen, no one can access it, protecting all of your personal information inside.
While these basic fundamental things will help prevent most hacking attacks, it ultimately is the user that personally invites the fox into the henhouse. Be diligent. Be vigilant. Be aware.
