The Age of Information created the Age of Cyber Crime
The Age of Information created the Age of Cyber Crime
Trying to remember a time before the World Wide Web, personal computers, iPads, and smart phones is comparable to trying to imagine a time before there were cars and highways. The advantages of the information age has allowed us to access and share massive amounts of information, perform commerce, and interact across diverse populaces on a grander scale than imagined when that first Apple PC was introduced in the late 1970s. However, as with all great technological advances, new dangers and threats emerge that we must defend against.
One such threat are cyber criminals. They lurk in the dark corners of the Internet waiting to steal your personal and private information. And human error is still one of the biggest reasons cyber criminals gain access to this information. So, this month we are kicking off a multipart series centered around cyber security. Each month we will be sharing helpful information on the different methods cyber criminals use to get your information and things you can do to help protect yourself.
Phishing anyone?
Email has become essential for everyday communication, both personally and professionally. So, it shouldn’t surprise you that it has also become one of the most common methods that cyber criminals use to get your sensitive information.
Phishing is when a cyber criminal sends a fraudulent email message that impersonates a trusted source. Because these emails look so real, they trick you into clicking on links, downloading harmful attachments, or entering personal information. In fact, Verizon found that 30 percent of all recipients open phishing email messages, and 12 percent click on the malicious links and attachments inside.
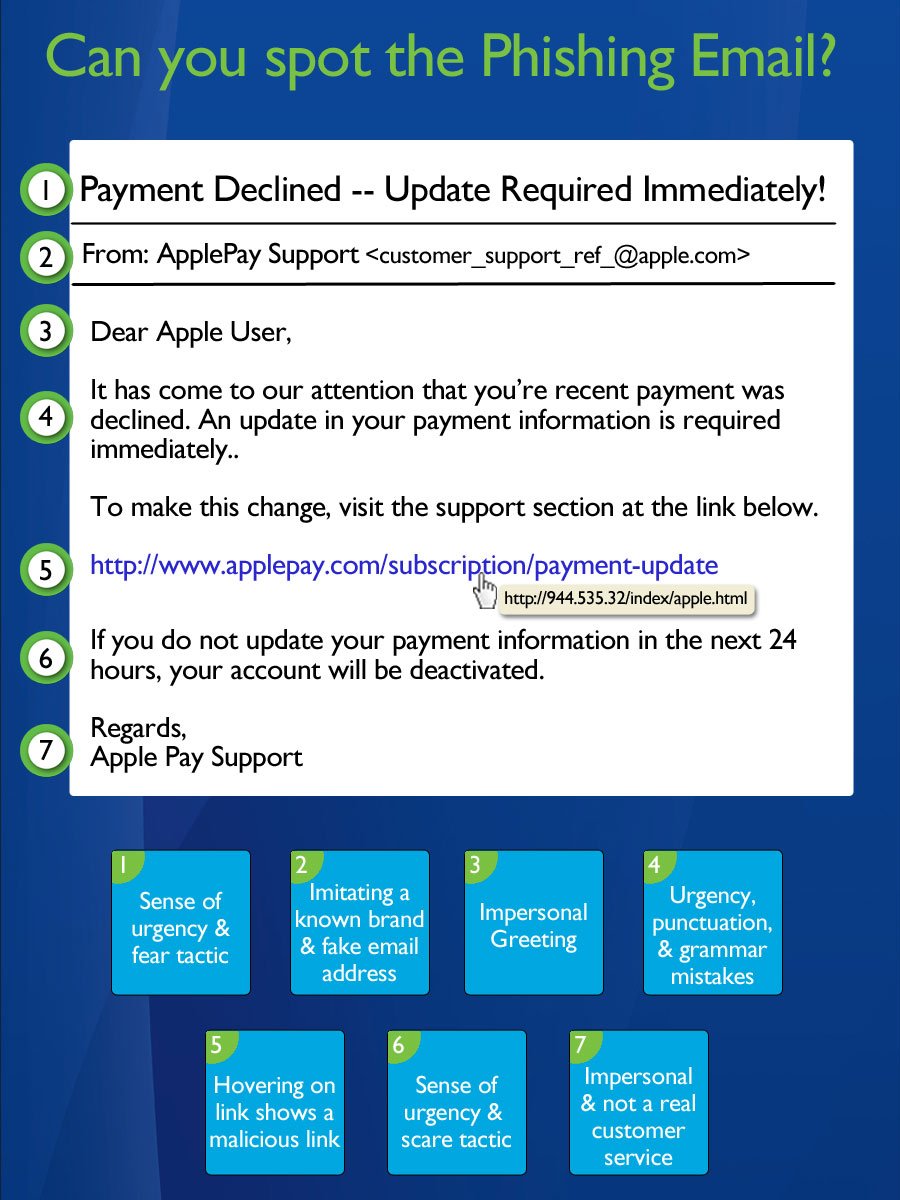
Many phishing emails are disguised to look like it is from a friend or family member. If it doesn’t feel right, check with the source of the email via a phone call, or sending a separate email. Also, carefully check out the email address of who it is from. Cyber criminals like to use email addresses that look very similar to well-known companies, brands, or people. For example: @Paypl.com, @ctibank.com, @amizon.com, or @facebok.com.
Cyber criminals also try to lure victims in by embedding malicious links in their emails. You should always hover your mouse over a hyperlink in the email, BUT don’t click on it. When you do this, a box will appear showing you the exact address where the link will take you. If the real URL address looks suspicious or doesn’t match what is displayed in the email, it’s probably a phishing attempt and you should delete the email.
Cyber criminals like to use scare tactics or urgency in their emails. This is to cause fear and concern to get you to click on a link or share personal information. If the email says “urgent action required, respond immediately,” or warns you that your “account has been compromised & will be closed,” it is likely a phishing email. Never hesitate to call the company directly to confirm if something is wrong.
Another thing to look for are generic greetings and closing in the email. A legitimate business that you have worked with before, likely knows your name and will use it in the email. They will also provide contact information below their signature so you can contact them back if needed.
Lastly, look for spelling, grammar, and punctuation errors in the email. Whenever a large company sends an official email, it has likely been reviewed and proofed by several people for mistakes before it is sent out. So, if you are finding these errors, it is likely a scam.
Now that you know what to look for, here is a sample of a phishing email. Can you spot all of the warning signs?